Booting explained: Types, instructions, and problems

Steps involved in booting
When you are booting up a server and encounter an error, it helps to know at which stage the booting failed to troubleshoot the error effectively instead of running around in circles. To help you understand the booting process better, let's go over the steps involved.
Power-on self test (POST)
In this test, when the power button is pressed, the system's power supply sends a signal to the motherboard and other components. The processor executes the basic input/output system (BIOS) or unified extensible firmware interface (UEFI) firmware instructions stored in the read-only memory (ROM).
Then, the BIOS or UEFI executes the power-on self test, which checks and starts the essential hardware components like the RAM, graphic card, and keyboard.
Depending on your system's configuration, BIOS or UEFI initializes system firmware settings like clock and hardware configuration. You can access the BIOS or UEFI setup page to specify boot order, secure startup, and many more features by pressing a specific key (usually the del or esc key).
Boot loader
The BIOS or UEFI then checks the configured boot order to find a bootable device, which could be a hard drive, SSD, or even USB drive. In enterprise conditions, network locations are also used as bootable devices.
From the bootable device, the BIOS/UEFI locates the master boot record (MBR) or the GUID partition table (GPT), which contains the partition information and points towards the boot loader. Then, the boot loader program is loaded into the system's memory and executed. The boot loader—GRUB for Linux and Boot Manager for Windows—is responsible for loading the OS kernel into the system's memory.
OS kernel loading
A kernel is the core component of the OS that manages resources and hardware interactions. If you have multiple OS kernels available to boot, the boot loader provides options to select which OS kernel to boot. Once the preferred OS kernel is chosen, it is loaded into the system memory.
OS initialization
The kernel initializes important components like process manager, memory manager, file systems, and device drivers. Device drivers are the interfaces between the detected hardware components like printers and display units.
System configuration
Linux and other Unix-based OSs: The init or systemd process starts first.
Microsoft Windows: The session manager smss.exe, client/server runtime subsystem csrss.exe, and then winlogon.exe processes are started in sequence.
Then, essential system services are started. Daemons, e.g., background processes, are then started, which takes care of network management, system logs (SysLogs for Unix-based and EventLogs for Windows), and user authentication.
User login
The last stage of booting is the user login. Once the graphical user interface (GUI) or command line interface (CLI) opens up, you can log in with your credentials. This starts the session manager and boots the system with your specific configurations and settings.
Types of booting
There are two primary boot types: cold boots and warm boots.
Cold booting
A cold boot, also known as a hard boot, is when the booting starts from a completely powered-off state. When you press the power button, the system performs a series of hardware checks and initializes the OS. This process involves loading the BIOS or UEFI firmware. Then it locates and loads the bootloader from the storage device. The bootloader loads the OS into memory, allowing the computer to become operational. Cold booting is essential for applying hardware changes, troubleshooting issues, and ensuring a fresh start for the system.
Warm booting
A warm boot, also known as a soft boot, is the process of restarting a computer without turning off the power. This is typically done by selecting the restart option from the OS's menu or pressing the reset button on the system if it has one. During a warm boot, the system reloads the OS and reinitializes the hardware components without performing a full power cycle. This method is often used to apply software updates, resolve minor system issues, or refresh the system's state without performing a complete shutdown. Warm booting is faster than cold booting and helps maintain system uptime.
Why is booting important?
Applying updates and patches: Many updates, especially those related to security and OSs, require a system reboot to be fully applied. This is covered in detail in our recent blog about patches. Without a proper boot, these updates may not take effect, leaving your systems and servers vulnerable to security risks.
Stability and performance: When you run your systems without rebooting for a while, you will see a considerable degradation in performance. This is due to too many stale processes consuming CPU resources and memory being used by processes that are no longer needed (for example, the %temp% folder). A system reboot clears the memory and terminates stalled processes.
The first step in troubleshooting: A system reboot can resolve various system or software related issues.
Applying configuration changes: Any major configuration change is completely applied only after booting.
Problems related to booting
Now that we've explored how critical booting is to servers, let's look at the common problems IT administrators face with the process.
Scheduling a reboot: Reboots are often performed outside business hours, or for businesses operating 24/7, it is done outside peak business hours. Scheduling and co-ordinating reboot schedules in a large IT environment can be a complex endeavor.
Reboot results: Maintaining an accurate log of server reboots, including their reason, timing, and the result, is essential for compliance and audit purposes.
Timely reboots: Systems exposed to external networks must be rebooted promptly to apply critical security patches.
Site24x7 server monitoring agent's role in booting
Our robust server monitoring agent comes with features that can help you with the complexities organizations face with booting.
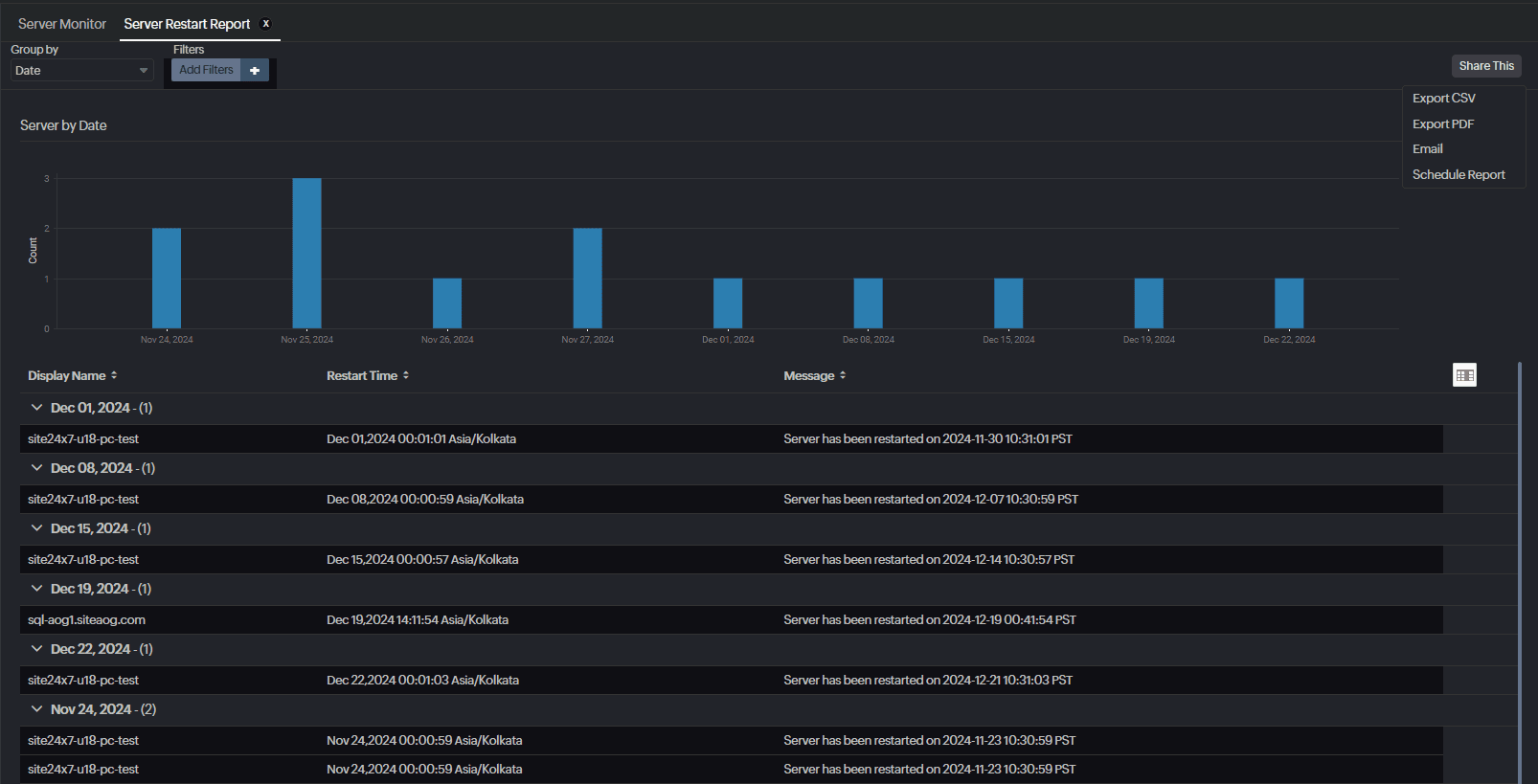
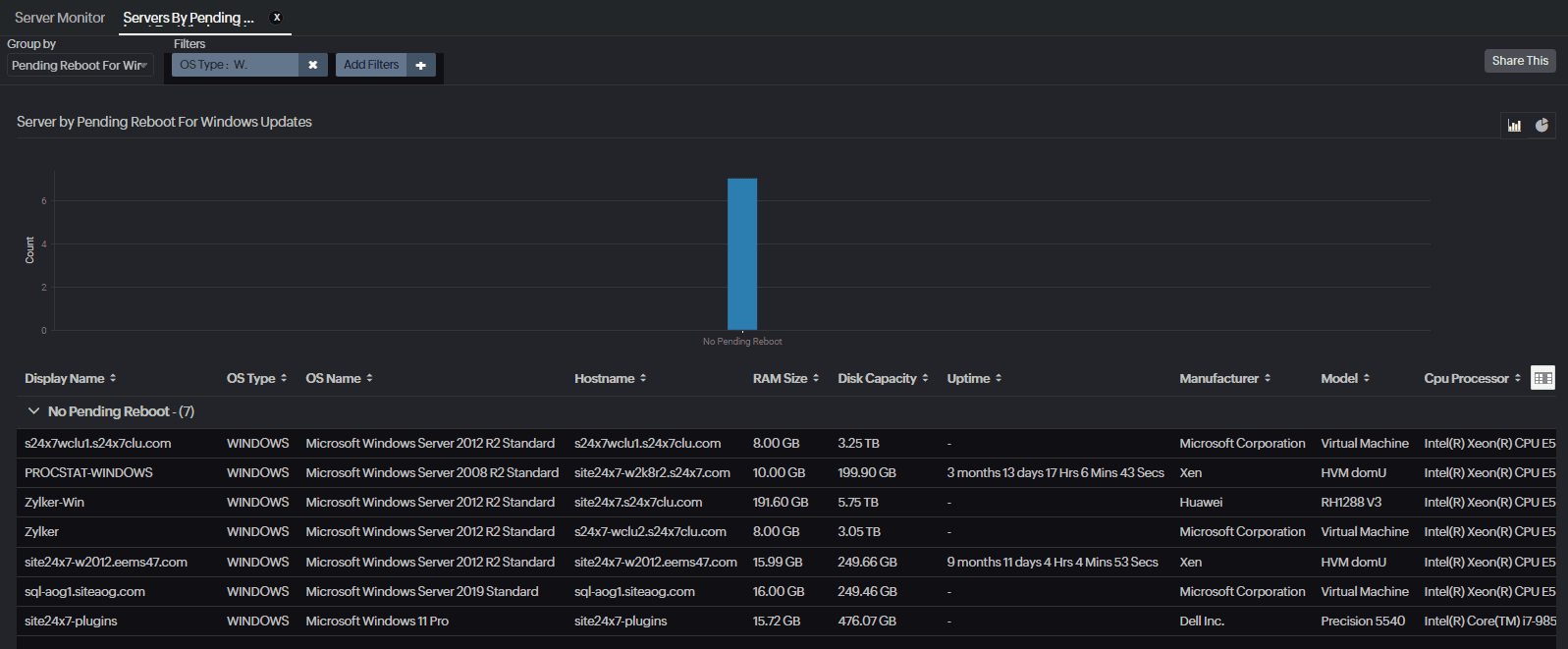
Our agent comes with automated reboot tracking. This keeps tabs on all the server and VM reboots in your environment. The Servers by Pending Reboot for Windows Update report saves hundreds of manual hours during compliance and auditing. Plus, you can get this report delivered straight to your inbox in specific intervals or on demand.
Struggling to know the specific servers that need a reboot to apply patches? Our agent can get you that information as well. The Servers by Pending Reboot report also lets you know which servers, VMs, or workstations require a reboot. Doing this manually in an IT environment consisting of thousands of hosts is like searching for a needle in a haystack—a task that is time and resource consuming without Site24x7 server monitoring.
We are compliant with every leading compliance standard like the GDPR, SOC 2, ISO 27001, HIPAA, and many more.
Every bit of data is handled with the utmost security standards.
Achieve operational efficiency with reports, dashboards, alerts, and analysis, all in one place.
Stay ahead of IT issues with our comprehensive AI-enabled server monitoring platform. Sign up for a demo that's tailored to your organization's needs and transform your server management efforts today.