On December 9, 2021, a new critical vulnerability CVE-2021-4422, also known as Log4Shell, was discovered in the popular Java logging library Log4j versions 2.0 to 2.14.1 that permits remote code execution (RCE), allowing attackers to execute arbitrary code on the host.
How vulnerable are your applications?
This vulnerability provides the loophole for attackers to execute codes remotely on any target computer that runs Log4j. It has also affected a few businesses by giving attackers the ability to hack systems, steal data, and install malware.
How does Site24x7 help businesses protect themselves?
Site24x7's top priority remains the security of our clients and products. In light of the recently discovered Log4j vulnerability (CVE-2021-44228), we have released a new version of APM Insight Java Agent that will detect if your application contains the Log4j vulnerability and notify you if so.
To avoid CVE 2021-44228 in your application, it is recommended that you update your Log4j library version to 2.17 or higher.
Here's a quick look at how we detect and alert you if your application is vulnerable to Log4j.
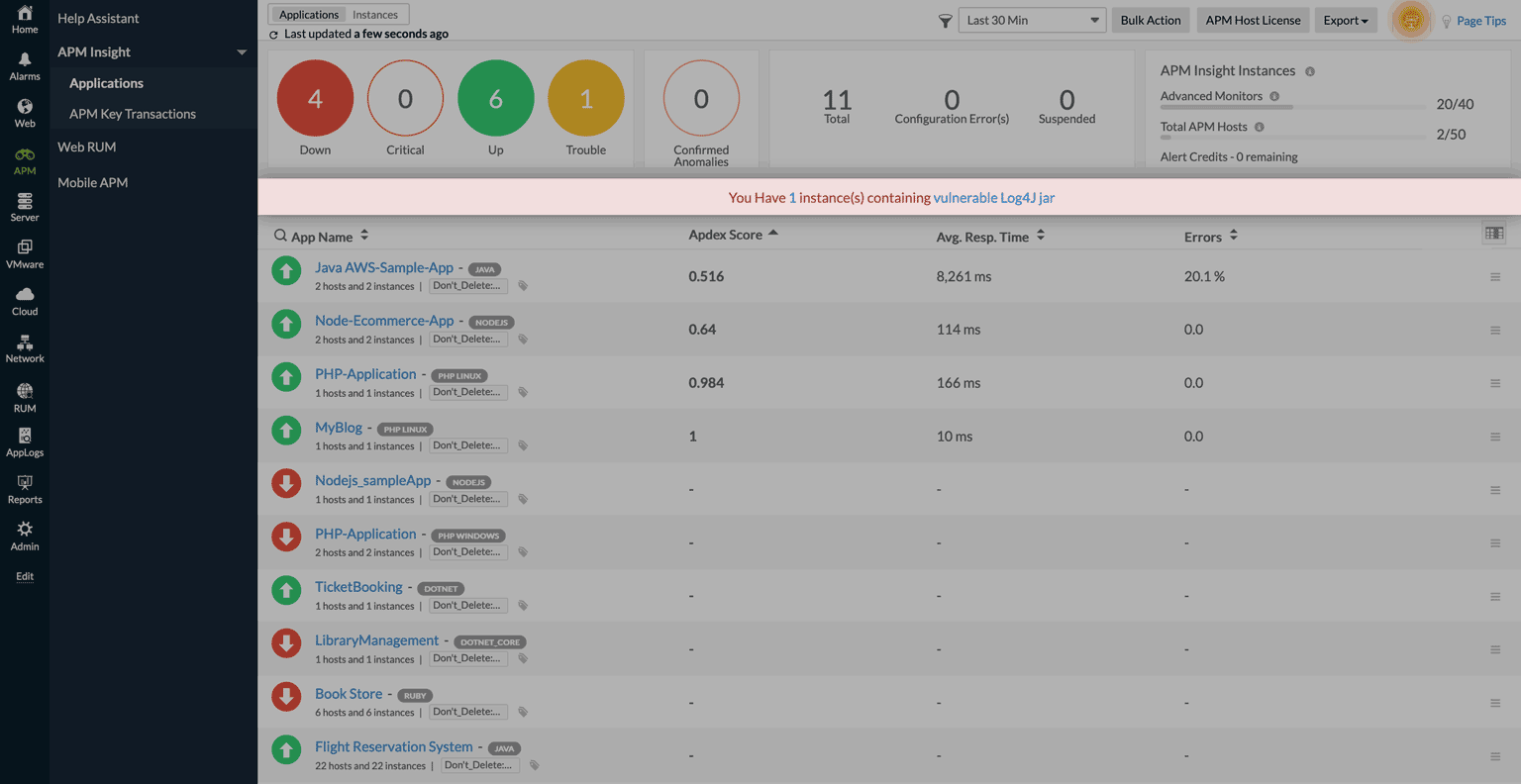
Not using Site24x7 yet? You can sign up now for a free, 30-day trial.
Java Agent installation
- Download and install the latest version of the Site24x7 APM Insight Java Agent based on the application server being used.
- Once the agent is installed, you can view the application monitor under APM > APM Insight > Applications.
Install this agent and test your applications for Log4j vulnerabilities. Fix them quickly to maintain a secure IT environment. Please leave your feedback in the comments section below.
Regards,
The Site24x7 team
This is very helpful!
And it would be even better if it finds the current spring4shell vulnerabilities.
Challenge accepted? ;)
Regards, Torsten
Thank you, Torsten.
Yes, we are also working on detecting Spring4shell vulnerabilities using our APM Insight Java agent. Soon, you'll be able to see the same in our product:)
We will keep you posted in this thread.
Regards,
Priya
Site24x7 Team
Hi there,
We are excited to announce the release of v5.5 of the APM Insight Java agent, which will detect and notify you if your application contains vulnerable versions of jars associated with the Log4j, Spring4Shell, and Spring Cloud RCE vulnerabilities.
To mitigate CVE-2022-22965 (Spring4Shell vulnerability) in your application, it is recommended that you upgrade the spring framework version to 5.3.18+ or 5.2.20+. All older versions are vulnerable.
To mitigate CVE-2022-22963 (Spring Cloud RCE vulnerability) in your application, it is recommended that you upgrade your spring cloud function version to 3.1.7+ or 3.2.3+. All older versions are vulnerable.
Here's a look at the dashboard where you can see the number of instances that contain any or all of these vulnerable jars (Log4j, Spring4Shell, or Spring Cloud RCE).
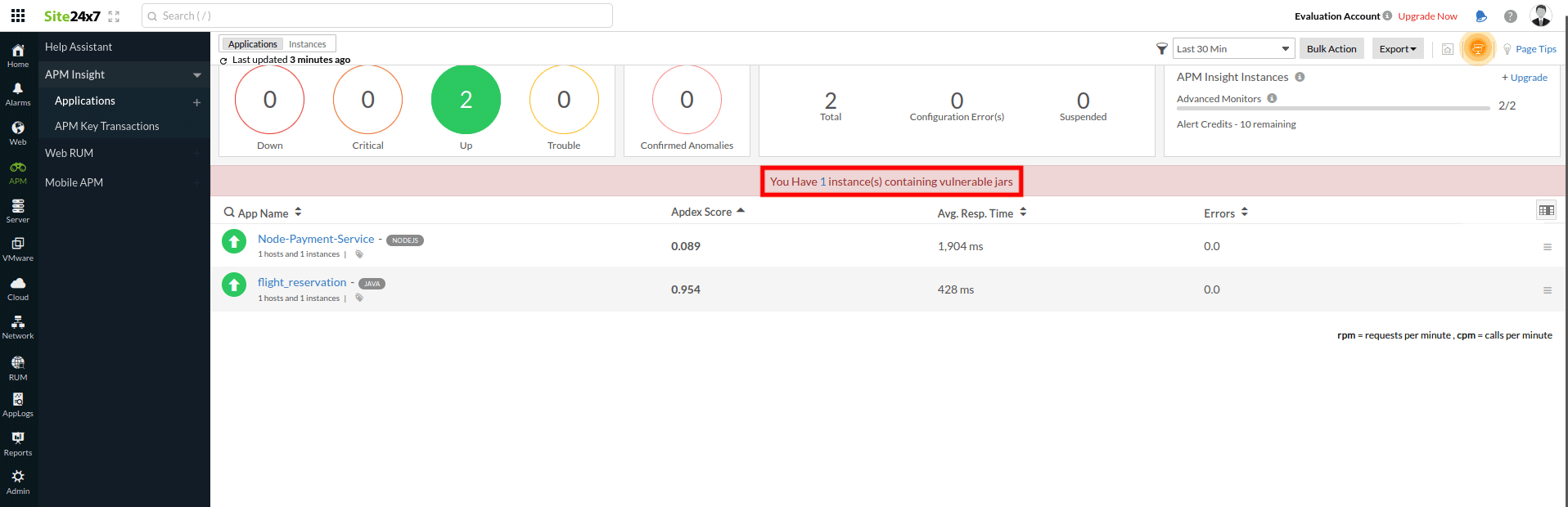
You can click on the instance count to get the list of instances. Open each instance to identify the exact vulnerability.
For example, The instance shown below has a Spring4Shell vulnerability.
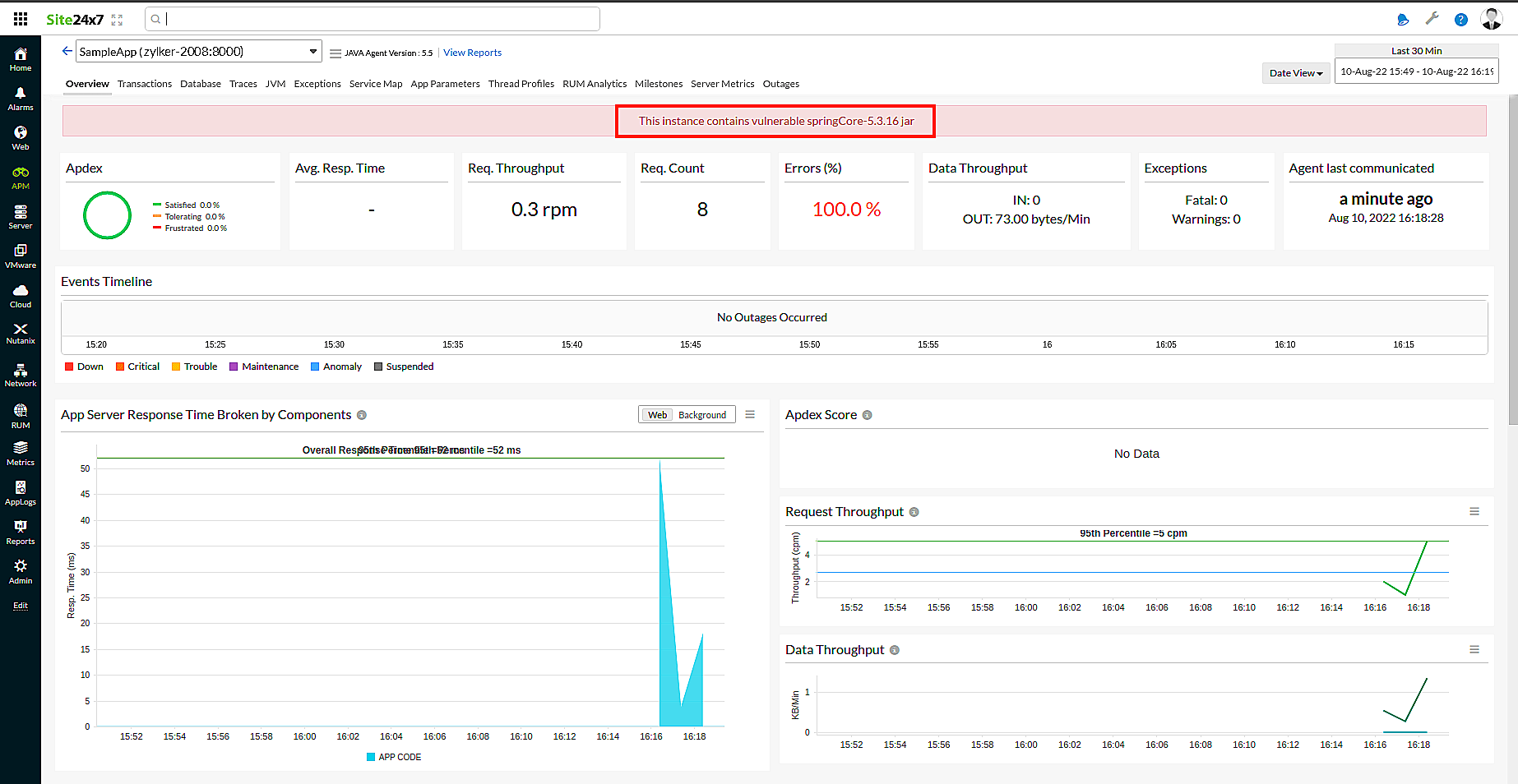
Regards,
Priya
Site24x7 Team